Shielding any cryptocurrency into a privacy coin
Shielding will be the process of transforming cryptocurrencies on other cryptonetworks (or “public coins”) into privacy coins on Chameleon.
Privacy coins
Through the Chameleon Network, a public coin will be shielded to obtain its privacy coin counterpart of the same value. For example, BTC will be shielded to obtain the privacy coin pBTC. pBTC will have the same value as BTC, so 1 pBTC can always be redeemed for 1 BTC and vice versa.
Once shielded, privacy coin transactions will be confidential and untraceable. A privacy coin on the Chameleon Network will offer the best of both worlds: it will retain the value of its original counterpart while being transacted confidentially on the Chameleon Network.
| PRIVACY COINS | COUNTERPART | NUMBER OF TRANSACTIONS |
|---|---|---|
| pBTC | BTC | 432,755 |
| pUSDT | USDT | 385,451 |
| pETH | ETH | 361,648 |
Table 1: The top three privacy coins on the previous network from 2019 to 2024.
Shielding
The shielding mechanism will be based on the experience of building the first-generation trustless bridge, inspired by the framework used between Chameleon and Ethereum. It will be generalized to enable a broader range of cryptonetworks to be interoperable with the Chameleon Network.
Current blockchain interoperability solutions will mostly involve building ad-hoc bridges. For example, BTC Relay [BTC Relay, 2019], WBTC [WBTC, 2019], and TBTC [TBTC, 2019] create specific bridges between Bitcoin and Ethereum, while Kyber Network builds Waterloo [Baneth, 2019], an ad-hoc bridge between Ethereum and EOS. For Chameleon, doing it ad hoc—one bridge for every cryptonetwork—will not be a scalable option.
Chameleon Network will take a different approach: build once, and work with any cryptonetwork. The shielding mechanism will operate via a general bridge design that connects Chameleon to a wide range of cryptonetworks, enabling secure bi-directional transfers of cryptocurrencies whenever privacy is required. This means any coin will be able to transform into a privacy coin. This approach will be particularly valuable for creating interoperability with cryptonetworks that do not support smart contracts, such as Bitcoin and Binance Chain.
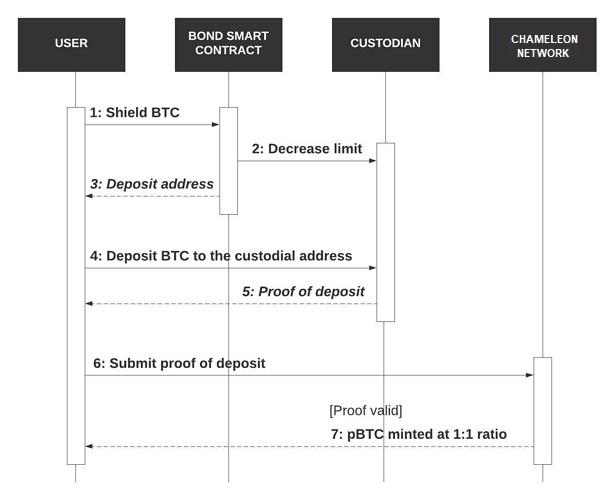
To obtain privacy coins, the user will first submit a shielding request to the Bond smart contract with details about which public coins they wish to shield and the amount. The Bond smart contract will then select trustless custodian
for the public coins and provide the user with the custodians’ deposit addresses. Once the deposit is confirmed on the cryptonetwork of the public coins, the user will initiate a shielding transaction on Chameleon along with the deposit proof. A deposit proof on a cryptonetwork will typically be a Merkle branch that links the deposit transaction to the block in which it is time-stamped, ensuring that the deposit transaction has been accepted by that cryptonetwork.
Note that while we have designed a general bi-directional bridge between Chameleon and other cryptonetworks, we still need to implement the specific SPV logic for each cryptonetwork we add to the bridge. This includes relaying block headers from those cryptonetworks to Chameleon and performing SPV on deposit proofs.
Chameleon validators will verify the shielding transaction and the deposit proof inside it, specifically using Simplified Payment Verification [Nakamoto, 2008]. Most cryptonetworks, including the Chameleon Network, will support Simplified Payment Verification with a few small differences in the underlying data structures. For example, Bitcoin and Binance will implement Merkle Tree [Merkle, 1980], while Ethereum will implement a modified Merkle Patricia Tree [Wood, 2014].
Once the deposit proof is verified, new privacy coins will be minted at a 1:1 ratio.
Other public coins follow the same shielding process. Note that we simplify step 5 to make it easier for readers to follow the main logic: the proof of deposit is not generated by the custodian but by the miners of the underlying crypto network.
Unshielding
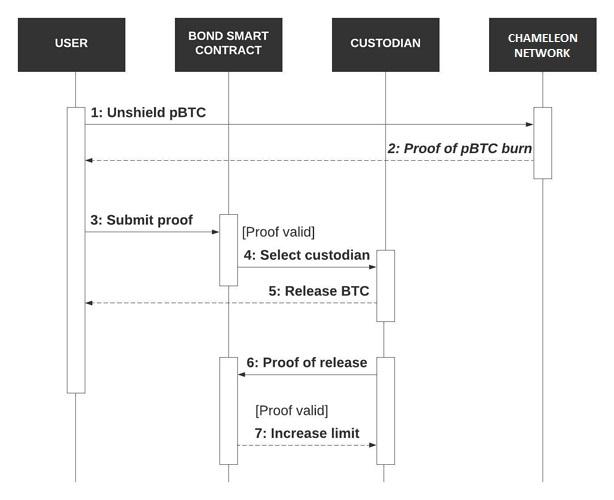
Unshielding will be the reverse process of shielding: turning privacy coins back into public coins.
The user will initiate an unshielding transaction on Chameleon with information about which privacy coins they want to unshield and the amount.
Chameleon validators will verify the unshielding transaction, burn the privacy coins, and issue a burn-proof. A burn-proof on Chameleon will be cryptographic proof. When signed by more than ⅔ of Chameleon validators, it will prove that the privacy coins have been burned on the Chameleon network.
The user will then submit the burn-proof to the Bond smart contract, which will verify the burn-proof and instruct a custodian to release the public coins that back those privacy coins at a 1:1 ratio. Once the release is confirmed on its respective crypto network, the custodian will submit the released proof to the Bond smart contract. Similar to the deposit proof, a release proof will be a Merkle branch linking the release transaction to the block it is time-stamped in, proving that the release transaction has been accepted by that crypto network.
After verifying the released proof, the Bond smart contract will free up the custodian’s collateral. Custodians will be able to withdraw their collateral or start taking new user deposits.
We will propose a mechanism for turning cryptocurrencies on other cryptonet works (or “public coins”) into privacy coins, based on a set of [trustless custodians]. Once shielded, privacy coin transactions will be confidential and untraceable. A privacy coin will enjoy the best of both worlds: it will retain the value of its original counterpart and can be transacted confidentially on the Chameleon Network.
An exception will be addressed in the Auto-Liquidation section in the Trustless Custodians
![Figure 1. SPV in Bitcoin [Nakamoto, 2008]. Other cryptonetworks employ similar SPV methods.](https://forum.chml.network/uploads/default/original/1X/edefe5f08a79f6c30300ecb69135c93cb80bb59c.png)